davin.50webs.com/research Bringing to you notes for the ages
A memory leak detection system for C++ Version II
Abstract
This article presents a memory leak detection system
called D.M.M. (Debug Memory Management ) for finding
memory leaks in C++ programs when the symbol NDEBUG is not set.
The system uses hash tables to keep track of allocated memory which is
an improvement on using arrays to keep track of allocated memory which
was what the earlier system used.
1. The system
Here is the enum_debug_code enum Here is the Root class Here is the single-inheritance supporting Single class :
Here is the multiple-inheritance supporting Multi class :
Here is the DMM header file dmm.hh :
Here is the DMM implementation file dmm.ch :
Here is the Array template class Here is the List template class Here is the List_Node template class Here is the List_Iterator template class Here is the Boolean bool wrapper class Here is the Integer int wrapper class Here is the Double double wrapper class and the
Float float wrapper class Here is the String string wrapper class
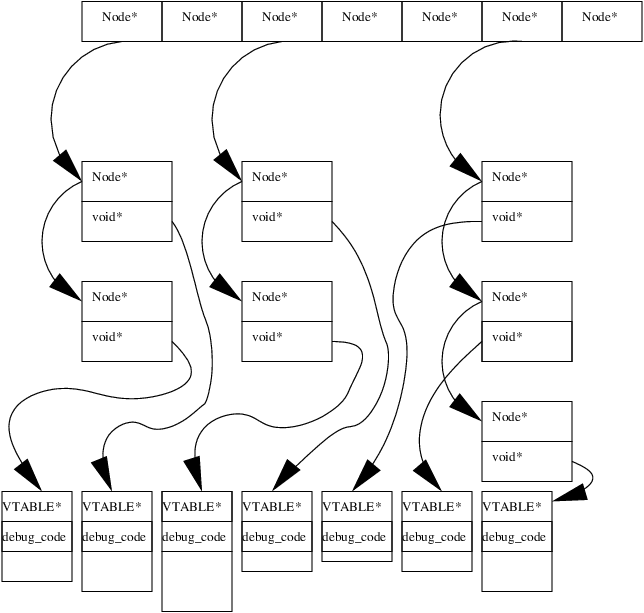
Here is a diagram of the hash table in action:
Note that the size of the array is a prime number. The index into the
array i is computed like so:
void * operator new (size_t size )
{
void * address = ::calloc(size,1);
unsigned int address_int = reinterpret_cast <unsigned int >(address);
unsigned int i = address_int % ARRAY_SIZE_PRIME_NUMBER;
Node * n = reinterpret_cast <Node *>(::malloc(sizeof (Node )));
ASSERT (n != null return address;
}
Here is operator delete:
void operator delete (void * p )
{
if (p == null unsigned int address_int = reinterpret_cast <unsigned int >(p);
unsigned int i = address_int % ARRAY_SIZE_PRIME_NUMBER;
Node * n_old = null for (Node * n = dmm_array[i]; n != null void * q = n->data;
if (q == p)
{
if (n_old == null null else
{
n_old->next = n->next;
}
ASSERT (n != null break ;
}
n_old = n;
}
::free(p);
}
debug_dmm_print function:
void debug_dmm_print ()
{
dmp ::cout << "[\n" ;
for (int i =0 ; i<ARRAY_SIZE_PRIME_NUMBER; i++)
{
for (Node * n = dmm_array[i]; n != null Root_G_C * r = reinterpret_cast <Root_G_C *>(n->data);
dmp ::cout << " " << dmm_decode(r->debug_code) << '\n' ;
}
}
dmp ::cout << "]\n" ;
}
Here is the dmm_decode function:
#undef DCODE_CASE
#define DCODE_CASE (var) case var: return #var ;
const char * dmm_decode (enum_debug_code code )
{
switch (code)
{
DCODE_CASE (DCODE_GENERIC );
DCODE_CASE (DCODE_BOOL );
DCODE_CASE (DCODE_INT );
DCODE_CASE (DCODE_QUICK );
DCODE_CASE (DCODE_FLOAT );
DCODE_CASE (DCODE_DOUBLE );
DCODE_CASE (DCODE_STRING );
DCODE_CASE (DCODE_XYI );
DCODE_CASE (DCODE_XYQ );
DCODE_CASE (DCODE_XYD );
DCODE_CASE (DCODE_V3I );
DCODE_CASE (DCODE_V3Q );
DCODE_CASE (DCODE_V3D );
DCODE_CASE (DCODE_BITMAP );
DCODE_CASE (DCODE_SAMPLE );
DCODE_CASE (DCODE_GULPER );
DCODE_CASE (DCODE_LIST );
DCODE_CASE (DCODE_LIST_NODE );
DCODE_CASE (DCODE_LIST_ITERATOR );
DCODE_CASE (DCODE_ARRAY );
DCODE_CASE (DCODE_MENU_BUTTON );
DCODE_CASE (DCODE_MENU_LIST );
DCODE_CASE (DCODE_SPRITE );
DCODE_CASE (DCODE_SPRITE_2 );
DCODE_CASE (DCODE_SPRITE_GRABBER_ACTION );
DCODE_CASE (DCODE_SPRITE_EDITOR_RECT );
DCODE_CASE (DCODE_WIDGET );
DCODE_CASE (DCODE_FILE );
DCODE_CASE (DCODE_TRI_RANDOM_OUTER );
DCODE_CASE (DCODE_TRI_INPUT_DEVICE );
DCODE_CASE (DCODE_TRI_PLAYER );
DCODE_CASE (DCODE_TRI_PONG_FADER );
DCODE_CASE (DCODE_TRI_PONG_BALL );
DCODE_CASE (DCODE_TRI_SLIMER );
DCODE_CASE (DCODE_TRI_STRATEGY );
DCODE_CASE (DCODE_TRI_TRICKS_NODE );
DCODE_CASE (DCODE_TRI_TRICKS );
DCODE_CASE (DCODE_TRI_PAIR );
DCODE_CASE (DCODE_R4_SAVE );
}
return "<Unknown>" ;
}
This page has the following hit count:
| Main Menu | Research Projects | Photo Album | Curriculum Vitae | The Greatest Artists | | Email Address | Computer Games | Web Design | Java Training Wheels | The Fly (A Story) | | Political Activism | Scruff the Cat | My Life Story | Smoking Cessation | Other Links | | Debugging Macros | String Class I | Linked List System I | Java for C Programmers | Naming Convention | | String Class II | How I use m4 | Strings III | Symmetrical I/O | Linked Lists II | | Run-Time Type Info | Virtual Methods | An Array System | Science & Religion | Submodes | | Nested Packages | Memory Leaks | Garbage Collection | Internet & Poverty | What is Knowledge? | | Limits of Evolution | Emacs Additions | Function Plotter | Romantic Love | The Next Big Thing | | Science Fiction | Faster Compilation | Theory of Morality | Elisp Scoping | Elisp Advice | | S.O.G.M. Pattern | Safe Properties | School Bullying | Charisma Control | Life and Death | | Splitting Java | Multiple Ctors | Religious Beliefs | Conversation 1 | Conversation 2 | | J.T.W. Language | Emacs Additions II | Build Counter | Relation Plotter | Lisp++ Language | | Memory Leaks II
| Super Constructors | CRUD Implementation | Order a Website Form | There Is An Afterlife | | Occam's Razor | C to Java Translator | Theory of Morality II | More Occam's Razor